Operations Guide
Overview
-
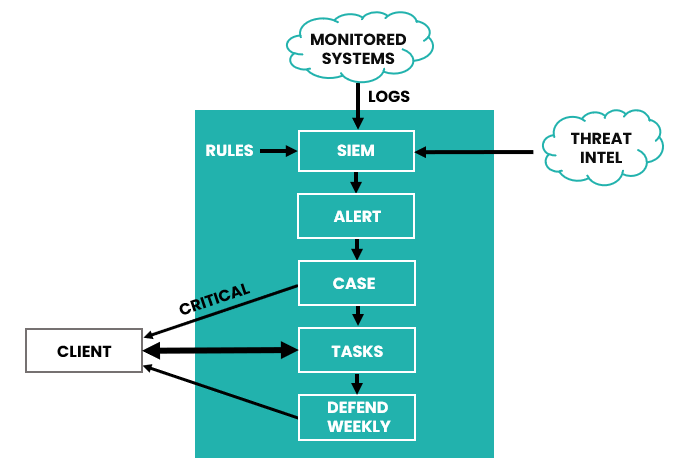
Each monitored system has an Agent sending log files to DEFEND.
-
DEFEND compares these logs against a set of Rules and the latest Threat Intelligence, and this generates ALERTS.
-
The SOC Team analyse these ALERTS, and if they require further investigation, open a CASE.
-
TASKS are added to each CASE, explaining any corrective measures that may need to be taken.
-
You will be emailed when a TASK is assigned to you, and updates to these TASKS can be added either via email or through the DEFEND Console.
-
If a CASE is of critical severity, then the SOC escalate it to your designated first point of contact.
-
A weekly report is emailed to you, listing
-
CASES INVESTIGATED
-
CURRENT VULNERABILITIES by device
-
SOFTWARE PACKAGES that are affected by these VULNERABILITIES
-
-
A more in-depth report is also sent out to you quarterly.